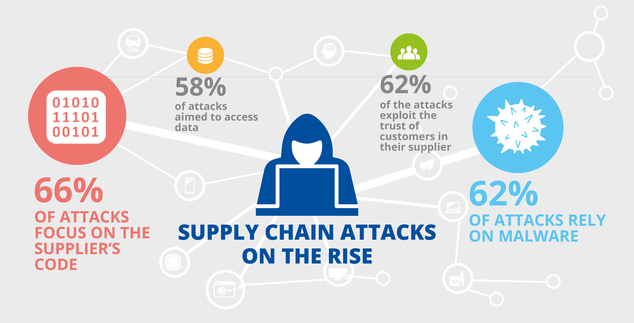
Checkmarx researchers have detected multiple open-source software supply chain attacks aimed at the banking sector in the first half of 2023. The attacks targeted specific components in web assets used by banks, and the attackers used advanced techniques.
In one attack, the threat actor using Social Engineering created fake LinkedIn profiles to get in touch with the victims' employees. They then used a specific C2 for each target. The contributor behind the malicious packages was linked to a LinkedIn profile page of an individual who was posing as an employee of the victim.
The two malicious npm packages employed in the April 2023 attacks included a preinstall script used to activate the multi-stage attack chain. In the first stage, the script determined the host operating system (Windows, Linux, or macOS) and downloaded the second-stage malware from a remote server by using Azure's CDN subdomain that included the name of the bank in question.
The use of Azure's CDN subdomains allows attackers to avoid detection and bypass traditional deny list methods.
The second-stage payload is the Havoc Framework, which provides post-exploitation capabilities like other more popular hacking tools, including Cobalt Strike, Sliver, and Brute Ratel.
In a second attack observed by the company in February 2023, threat actors targeted a different bank. The attackers uploaded a malicious npm package that contained a masterfully crafted payload designed to blend into the website of the victim bank and lay dormant until it was prompted to spring into action.
The payload revealed that the attacker had identified a unique element ID in the HTML of the login page and designed their code to latch onto a specific login form element, stealthily intercepting login data and then transmitting it to a remote location.
The experts believe that the two attacks are not linked, and the npm packages have been reported and subsequently removed. The names of these packages were not revealed.
Checkmarx believes that we will observe a steady escalation in such kinds of targeted attacks, including on banks. The report published by Checkmarx includes indicators of compromise (IoCs) for these attacks.
Takeaways
The banking sector is a prime target for supply chain attacks.
Attackers are using advanced techniques to bypass traditional security measures.
Organizations need to be aware of the risks and take steps to protect themselves.
Recommendations
Conduct regular security assessments of third-party vendors.
Implement security awareness training for employees.
Use strong passwords and multi-factor authentication.
Keep software up to date.
By following these recommendations, organizations can help to protect themselves from supply chain attacks.


